Phishing is nothing new to most web users nowadays, but despite how aware we are, there will always still be people who get caught unaware by them, even I was almost fooled once.
What is Phishing?
Phishing mails had came a long way from simple autonomous plain-text mails to nicely detailed craft emails from various banks or monetary organizations. They are all made to appear like official emails to cheat or exploit their victims. Thankfully, most phishing emails often appear obviously different from the genuine ones. Though there are some exceptionally very good ones which mimics the official email letterhead on top of masking emails and sender’s addresses.
I found this of a concern as I believe that almost most people out there are users of these few payment or banking services. Thus, there will bound to be exploits and cause for concern. Here are 3 “rather commendable” emails I’ve received personally myself to date which I will be using as examples for my illustration:
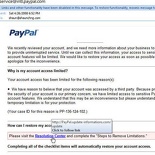
Phishing example one- Paypal account deactivation
For long, paypal has always emphasized that they do not send out any emails to users with regards to asking for personal account information. The only time you will get an official email from them is upon registration. Possible account “problems” with your account, especially if you have recently used it do not come out of the blue.
This email I’ve received is one the best ones I’ve got which looks almost like the real thing. With proper image headers, support, contact and paypal addresses at the email footer as well. It simply amazes me is how professionally laid out it is and how phishing emails had came through. This particular ones states you account has been suddenly deactivated and have to follow up to their “resolution center” with your login details to verify your account so it can you it again- very cunning.
Check linked email URLs for authenticity
Upon closer inspection in the HTML coded URL address, it actually points to a site other than paypal.com. So a good habit in outlook is to hover over any hyperlinks to see which root domain is it actually pointed to (in this case one called “update-informations.com” with a “paypal” subdomain). I can presume that these cheaters also use the same domain for other banks simply by changing the subdomain, e.g. HSBC.update-informations.com or CITI.update-informations.com.
A general rule is anything originating from your bank’s root or top-level domain (TLD) are genuine addresses. This includes it’s subdomains (e.g. anything before the “.” like sgsubs.subway.com- “sgsubs” is the subdomain), to the domain name (or mid level domain MLD) itself (e.g. subway.com) and subfolders. Anything following after the slash “/” from the TLD (e.g. subway.com/blt_special), with the following examples you can test yourself with.
Examples distinguishing real and fake TLDs:
- https://anything.paypal.com = Real (though they seldom use subdomains)
- https://www.paypal.com = Real
- https://www.paypal.com/cgi-bin = Real
- http://login.data.paypal.com = Fake (masked MLD)
- https://paypal.com.survey-infos.com = Fake (another masked MLD)
Moreover, another good way to tell you are on a real site is the presence of secure http, or the secure hypertext protocol denoted by https:// before your actual URL. The absence of a website icon can also be a give away as well. You can read more in relations to paypal at their Security Center.
Bank users are targeted too
I’ve received similar official looking emails from “HSBC” and “Bank of America” as well. However, these emails are more or less based on the similar hit-and-run principal. In other words, you can’t fool people unless you are either a member of any of those banks. It was a dead giveaway for me as I was neither a HSBC or Bank of America member, so something was definitely amiss.
Such emails can take few over forms as well, such as asking you to update your personal particulars (e.g routine update, survey, etc) to an email warning you of unauthorized account access, alerting you to “login” immediately to rectify the problem. Remember, banks WILL not ask you for account information through email, they will always mail it to your physical home addresses.
When in doubt, ALWAYS call your bank to confirm the email before proceeding or even providing any personal information, and please do yourself a favor by not calling the phone numbers listed in the phishing email itself.
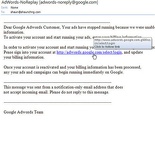
Example case two- Update my Google Adsense details?
Being a Google advertising user myself, I believe most users will simply pounce at any official email sent from them. But won’t all members be confirmed of their details through snail mail and only at the point of registration?
Why the email out of the blue? In fact, these emails will be the same for other “problems” to get your attention to act, such as account intrusion, account deactivation, etc… Sneaky…
The page is made to look like a standard plain text email, but it is infact HTML coded, so the URLs shown are not the true URLs. As suspected, what appears to be a link pointing to http://adwords.google.com/ is rather, directed to a subdomain with “adwords.google” on the root domain “g500oz.cn”, a China registered website. Now ain’t that sneaky or what?
Hidden sender’s email- who actually sent the email?
At a glance, the email header reads, “adwords-noreplay [adwords-noreply@google.com]”, though the word “replay” is already a big giveaway, do note that sometimes phishers put a true-looking email as their sender’s email name (where we normally put to address names such as “John Tan”, or “Jennie Tay”). This is a flaw in outlook as it will automatically renders the next best available thing- if a name is provided, it will show the name, if not an email will be shown. Doing it seemlessly by default may allowing phishers to mask the true senders “from” email address from the user’s view unless you view the actual message properties. So, in all do not trust what you see in the outlook headers, especially if you suspect the source of it.
Encoded/variable URLs – do not click!
This URL however (adwords.google.com.g500oz.cn/select/Login), is safe if you accidentally click on it. As the most just your browser type, screen resolution settings and IP address (which gives geographical info) can be captured which actually means nothing to them. Thereafter, the most you will be directed to is a “ripped” login site made to look like the host’s site where “logging” won’t get you anywhere, but all your real login data captured and stored to be later exploited.
However, if you were to encounter a link however one in the format: “www.phishingsite.com/webscr?cmd=_your@email.com” or with your@email.com replaced with a numerical id such as “file.php?=&id=232137” with a question mark character tied to a variable/parameter (I have an example in the following case 3), these will actually send a verification back to the phisher/spammer server indicating that your email is indeed active. You can only expect more spam to come your way when that happens.
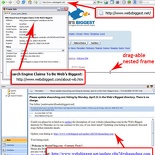
Example Case three- websbiggest.com or websbiggest.net?
This example is not much of phishing case but simply one of the most ingenuous ones I came across in verifying your active email. It’s very interesting one and I will believe will fool most users due to the very legitimate look of the domain name and how the site appears to look.
The email I’ve received from them has an encoded URL for me to click and “verify” my search engine submission, going by “websbiggest.net/update.cmf?d=shaunchng.com”. It’s outright, not hidden and is a legitimate top level domain (TDL), seems to be OK with no problems and most webmasters would simply pounce on free search engine submission.
I however, copied the TDL “websbiggest.net” and pasted that in my browser for verification, the page loads and it appears completely normal. Upon closer inspection, the URL I was directed too was perfect (www.websbiggest.net) and no hidden subdomains or HTML overwritten hyperlinks just like in the adsense and paypal email. I was paranoid, as it was a completely legitimate and functional search engine, till I started mouseovering all their links and they all point to the “http://websbiggest.com/” domain. Got ya!
Unfamiliar services is a quick red flag
Besides having a keen eye for detail (or you will miss this one), knowing the web services you had used before, and having some background knowledge of your search engine submissions will be useful as well. I’ve never added my site on the webbiggest.com search directory. However, “they” had sent me a rather looking legitimate email with a full site description of my site (presumably taken from my site’s meta description or google cache). I verified that the .net TDL and the .com TDL are indeed 2 separate identities.
In other words, the search engine with the .com top level domain (TLD) is real, but the page with the different .net TLD is actually a container housing the .com site inside it so it appears active. Another way to verify this is to check the page info (firefox) or page properties (in IE) by right clicking the page. People using internet explorer can only do so by selecting “view source” on the page they right click on, where firefox will allow you to view the source of specific frames- prompting you that the page you are viewing has nested frames.
A closer look at the domain registrar verfies my claim, the legitimate .com domain has a proper DNS and nameserver: NS1.WEBSBIGGEST.COM and NS2.WEBSBIGGEST.COM while websbiggest.net is registered with all similar “ripped” contact details. Only that the account is registered anonymously and pointed to nameservers from DirectInc, (NS0.DIRECTNIC.COM and NS1.DIRECTNIC.COM) a budget webhost based in New Orleans, LA.
What amazes me is the extent and measures phishers take into creating their phishing emails directed to their “cheat sites”, this one is a good example.
When encountering such emails, just simply ignore and delete them and you will be safe. Do not attempt to reply them too.
In conclusion, I hope this article with these few examples helps you into your awareness of phishing emails. Especially how to properly handle them despite resembling like their legitimate counterparts. It will be sometime before phishers get their capabilities up again and that is only when arming ourselves- the end user with these basic habits. This is where we can minimize exploits and fraud not only for yourself but for your immediate loved ones as well.


Never trust any links in HTML emails ever! I received a lot of phishing emails trying to trick me with CITIBANK. Then it swapped over to Google Adwords phising scam.
yea, its quite interesting that you can get phishers posing as representatives from almost any bank out there, and they all originate from the same few domains!
I get tons of Phishing emails, but what percentage of these emails are considered as “legitime” for others, perhaps there is one victim of one millon of these emails?
yup, I there will sure to be one or two who are “new” to the net and are not experienced enough to see through these messages. I remembered telling my parents (who only a few years ago recently only learnt how to use the net) of all of these dangers as well.
Hello Shaun,
I am so grateful for the effort you make to put out this info. I was tempted to reply to the email asking me to update my web info from worldsbiggest.org. As you say it looks like the real thing, but I am now going to ignore and delete. You do a great service to those of us more inexperiencedin the phishing world. I thank you, Blanche
Hello Shaun,
I also received a request from larry@healthhaven.com to include my website with healthhaven. Is it a bona fide site? Thanks, Blanche
Hi Blanche, well it depends, if you can get listed without the need to specify any personal information or make any payment, I don’t see any wrong to submitting your public-safe website details to them.
From the email you’ve provided, it does look legitimate. However, do note that there is the possibility of that email being “hijacked” from it’s rightful owner, so when submitting your info, do verify the URL of the website your are submitting on.